2016/09 New Microsoft 70-411: Administering Windows Server 2012 R2 Exam Questions Released Today!
Free Instant Download 70-411 Exam Dumps (PDF & VCE) 445Q&As from Braindump2go.com Today!
100% Real Exam Questions! 100% Exam Pass Guaranteed!
1.|2016/09 Latest 70-411 Exam Dumps (PDF & VCE) 445Q&As Download:
http://www.braindump2go.com/70-411.html
2.|2016/09 Latest 70-411 Exam Questions & Answers:
https://drive.google.com/folderview?id=0B75b5xYLjSSNfnNyWDFTYllvTTkteG0waVJYSFdoaDVWZTBSamh6Q0xiaUJmNEk5cUJSbFU&usp=sharing
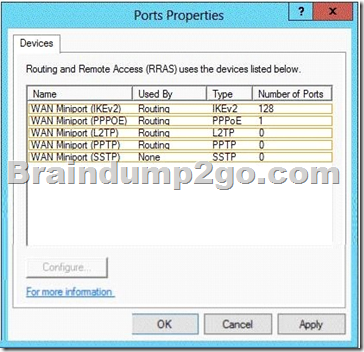
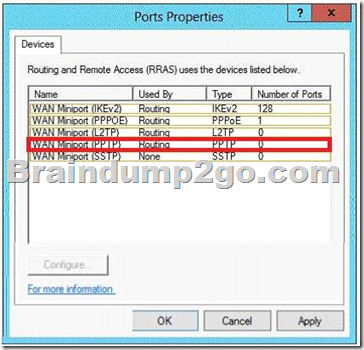
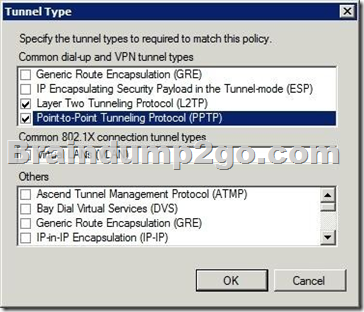
QUESTION 37
Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1 that runs Windows Server 2012 P.2. Server1 has the Network Policy and Access Services server role installed.
Your company’s security policy requires that certificate-based authentication must be used by some network services.
You need to identify which Network Policy Server (NPS) authentication methods comply with the security policy.
Which two authentication methods should you identify?
(Each correct answer presents part of the solution. Choose two.)
A. MS-CHAP
B. PEAP-MS-CHAP v2
C. Chap
D. EAP-TLS
E. MS-CHAP v2
Answer: BD
Explanation:
PEAP is similar in design to EAP-TTLS, requiring only a server-side PKI certificate to create a secure TLS tunnel to protect user authentication, and uses server- side public key certificates to authenticate the server. When you use EAP with a strong EAP type, such as TLS with smart cards or TLS with certificates, both the client and the server use certificates to verify their identities to each other.
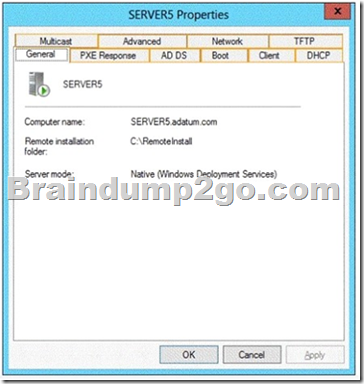
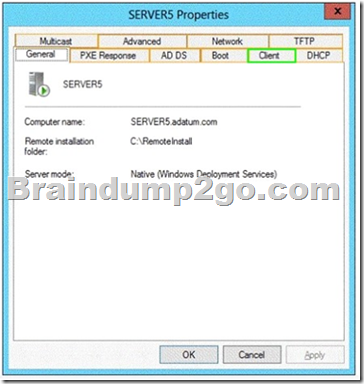
QUESTION 38
You have a server named Server1 that runs Windows Server 2012 R2. Server1 has the Windows Deployment Services server role installed.
Server1 contains two boot images and four install images.
You need to ensure that when a computer starts from PXE, the available operating system images appear in a specific order.
What should you do?
A. Modify the properties of the boot images.
B. Create a new image group.
C. Modify the properties of the install images.
D. Modify the PXE Response Policy.
Answer: C
Explanation:
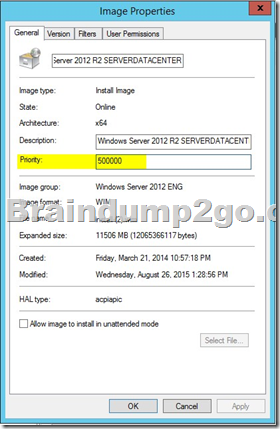
installation images are the operating system images that you deploy to the client computer. Start images are the images with which you start a client computer to perform an operating system installation. Boot images contain Windows PE and the Windows Deployment Services client.
The order of the display of images can about the value of priority on the register general are controlled in the properties of the images:
QUESTION 39
Your network contains an Active Directory domain named contoso.com. Domain controllers run either Windows Server 2008, Windows Server 2008 R2, or Windows Server 2012 R2.
You have a Password Settings object (PSOs) named PSO1.
You need to view the settings of PSO1.
Which tool should you use?
A. Get-ADFineGrainedPasswordPolicy
B. Get-ADAccountResultantPasswordReplicationPolicy
C. Get-ADDomainControllerPasswordReplicationPolicy
D. Get-ADDefaultDomainPasswordPolicy
Answer: A
Explanation:
A. Gets one or more Active Directory fine grained password policies.
B. Gets the resultant password replication policy for an Active Directory account.
C. Gets the members of the allowed list or denied list of a read-only domain controller’s password replication policy
D. Gets the default password policy for an Active Directory domain. http://technet.microsoft.com/en-us/library/ee617231.aspx
ttp://technet.microsoft.com/en-us/library/ee617227.aspx
http://technet.microsoft.com/en-us/library/ee617207.aspx
http://technet.microsoft.com/en-us/library/ee617244.aspx
QUESTION 40
You have a failover cluster that contains five nodes. All of the nodes run Windows Server 2012 R2. All of the nodes have BitLocker Drive Encryption (BitLocker) enabled.
You enable BitLocker on a Cluster Shared Volume (CSV).
You need to ensure that all of the cluster nodes can access the CSV.
Which cmdlet should you run next?
A. Unblock-Tpm
B. Add-BitLockerKeyProtector
C. Remove-BitLockerKeyProtector
D. Enable BitLockerAutoUnlock
Answer: B
Explanation:
Add an Active Directory Security Identifier (SID) to the CSV disk using the Cluster Name Object (CNO) The Active Directory protector is a domain security identifier (SID) based protector for protecting clustered volumes held within the Active Directory infrastructure. It can be bound to a user account, machine account or group. When an unlock request is made for a protected volume, the BitLocker service interrupts the request and uses the BitLocker protect/unprotect APIs to unlock or deny the request.
For the cluster service to selfmanage BitLocker enabled disk volumes, an administrator must add the Cluster Name Object (CNO), which is the Active Directory identity associated with the Cluster Network name, as a BitLocker protector to the target disk volumes.
Add-BitLockerKeyProtector <drive letter or CSV mount point> –
ADAccountOrGroupProtector – ADAccountOrGroup $cno
QUESTION 41
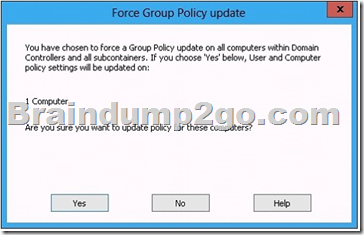
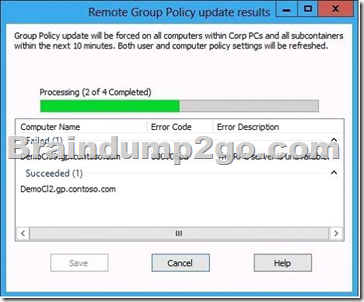
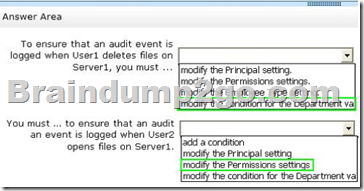
Hotspot Question
You have a file server named Server1 that runs Windows Server 2012 R2.
A user named User1 is assigned the modify NTFS permission to a folder named C:\shares and all of the subfolders of C:\shares.
On Server1, you open File Server Resource Manager as shown in the exhibit. (Click the Exhibit button.)
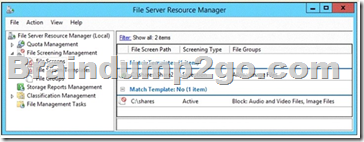
To answer, complete each statement according to the information presented in the exhibit.
Each correct selection is worth one point.
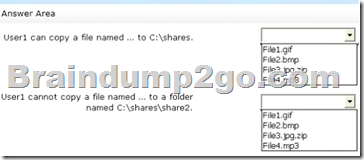
Answer:
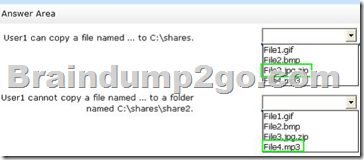
Explanation:
You can create file screens to prevent files that belong to particular file groups are saved on a volume or in a folder structure. A file screen affects all folders in the specified path. For example, you can create a file screen to prevent users from storing audio and video files in their personal folders on the server. You can also Resource Manager File Server configure that it sends e-mail or other notifications when a certain file screening event occurs.
A file screen can be active or passive:
Active checks prevent users from saving unauthorized file types on the server.
In passive checks users are monitored, save certain file types, and configured notifications
generated, users are not prevented from saving the files.
A file screen prevents users and applications not from accessing files that were saved in a directory before the file screen was created – regardless of whether the files belong to the blocked file groups or not. In the folder C: \ Data1 can no audio and video files and any image files are stored. Because except for image files to the directory C: \ Data1 \ Folder1 image files any audio and video files can be stored in this folder while but.
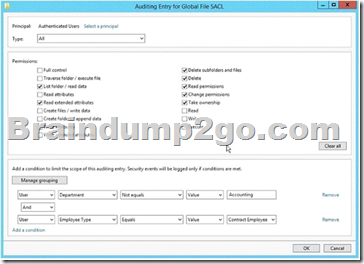
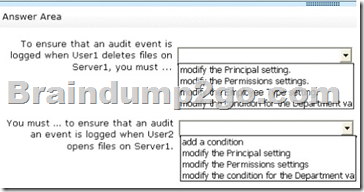
QUESTION 42
Your network contains an Active Directory domain named contoso.com. The domain contains 30 user accounts that are used for network administration. The user accounts are members of a domain global group named Group1.
You identify the security requirements for the 30 user accounts as shown in the following table.
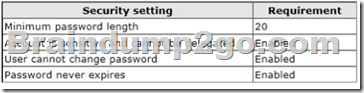
You need to identify which settings must be implemented by using a Password Settings object (PSO) and which settings must be implemented by modifying the properties of the user accounts.
What should you identify?
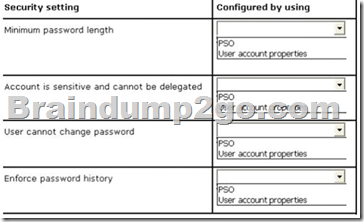
Answer:
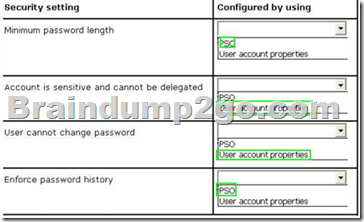
Explanation:
With the settings Account is sensitive and can not be delegated, and users can not change password is account options on the Register account can be activated in the properties of user accounts. In the settings Minimum password length and enforce password history is it to password policies that can be configured as part of a PSO object.
!!!RECOMMEND!!!
1.|2016/09 Latest 70-411 Exam Dumps (PDF & VCE) 445Q&As Download:
http://www.braindump2go.com/70-411.html
2.|2016/09 Latest 70-411 Exam Questions & Answers:
https://drive.google.com/folderview?id=0B75b5xYLjSSNfnNyWDFTYllvTTkteG0waVJYSFdoaDVWZTBSamh6Q0xiaUJmNEk5cUJSbFU&usp=sharing